Enhancing Cybersecurity: A Comprehensive Guide to Robust Security Measures
In the rapidly evolving digital world, securing sensitive data and mitigating cyber risks is critical for organizations. To protect valuable assets and maintain regulatory compliance, it's essential to prioritize cybersecurity measures. This captivating guide explores key security requirements, including identity management, detective controls, infrastructure security, data protection, and incident response. By implementing these measures, organizations can establish a robust security framework to combat cyber threats effectively.
Security Framework:
To build a strong security foundation, organizations must meet specific requirements. Let's dive into the essential security requirements.
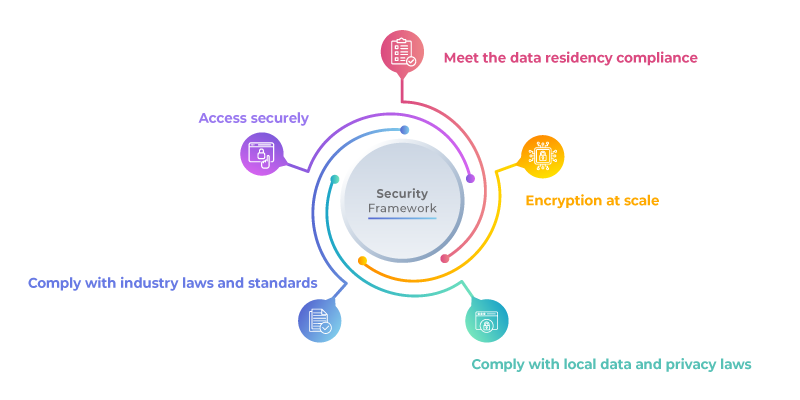
Meet the data residency compliance:
Complying with data residency regulations is crucial, especially when operating in multiple regions. By ensuring that data remains within specified boundaries, organizations can adhere to local regulations and address concerns related to data sovereignty and privacy.
Encryption at scale:
Encrypting data at scale is a vital aspect of security. By using encryption safeguards like cryptographic algorithms to render data unreadable to unauthorized users, organizations can protect sensitive information both at rest and in transit.
Comply with local data and privacy laws:
Adhering to local data protection and privacy laws is essential for maintaining customer trust and fulfilling legal obligations. Organizations must handle data properly, manage consent, and implement necessary measures to safeguard personal information.
Comply with industry laws and standards:
Different industries have specific regulations and standards that organizations must meet. Compliance with industry-specific regulations, such as HIPAA for healthcare, PCI DSS for the payment card industry or GDPR for data protection in the European Union, ensures data integrity and security.
Access securely:
Controlling access to systems and sensitive data is paramount. Strong authentication mechanisms, access controls, and the principle of least privilege help prevent unauthorized access. Additional security measures, such as multi-factor authentication (MFA) and conditional access policies, further enhance security.
Framework components:
Let’s now explore specific security components and discover best practices within each area.
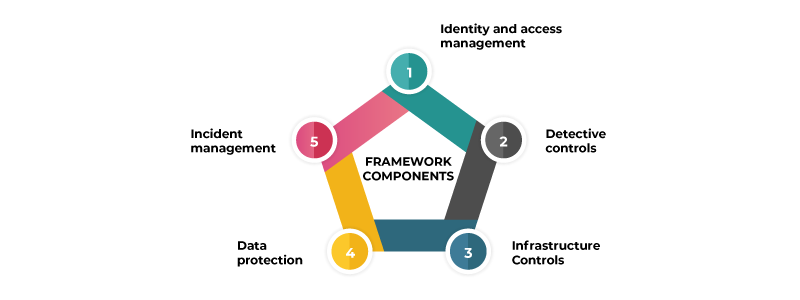
1. Identity and Access Management:
Robust identity management ensures proper access control and reduces the risk of unauthorized access. Implementation of the key aspects enhances security.
Key aspects include:
- Role-based policies: Defining access permissions based on user roles and responsibilities.
- User groups: Organizing users into logical groups to streamline access management.
- Policy definitions: Clearly defining policies and access rules to enforce security protocols.
- Credential management: Ensuring proper management of user credentials, including secure storage, rotation, and revocation.
- Password policy: Implementing strong password policies to enforce password complexity and periodic changes.
- MFA/Conditional access: Enabling Multi-Factor Authentication and setting conditional access policies based on user context and risk factors.
2. Detective Controls
Detective controls to monitor activities, enforce compliance, and identify potential threats.
Key aspects include:
- User activity monitoring: Monitoring and analyzing user activities to identify suspicious behaviour or policy violations.
- Compliance enforcement: Enforcing compliance requirements and identifying any deviations from established policies.
- Intrusion detection (zero trust): Adopting a zero-trust approach to continuously monitor for potential security breaches.
- Data retention/archival: Establishing policies for data retention and archiving to comply with legal and regulatory requirements.
- Asset inventory: Maintaining an up-to-date inventory of assets to ensure comprehensive security management.
- Automated cloud compliance: Leveraging automation to streamline compliance processes and reduce manual efforts.
- Stacks logs: Managing stacks logs is important to identify the threats and breaches.
3. Infrastructure Security:
Security infrastructure components are crucial for protecting systems and data.
Key aspects include:
- WAF/Firewall: Deploying web application firewalls and firewall solutions to secure ingress traffic.
- ACLs: Implementing access control lists with specific CIDR blocks to control routing table access.
- OS hardening & patching: Configuring operating systems to minimize exposure to threats and regularly applying patches.
- Service level controls: Defining controls and standards for services and systems to ensure consistent security practices.
- Host security: Implementing security measures at the host level, including intrusion prevention systems, antivirus software, and secure configurations.
- Service level security: Ensuring security measures align with service-level agreements (SLAs) to maintain a secure environment.
4. Data Protection:
Implementing encryption measures ensures data classification, securing data at rest and in transit, establishing a robust key management system, and managing digital certificates contribute to effective data protection.
Key aspects include:
- Data classification: Categorizing data based on its sensitivity enables organizations to apply appropriate security controls and protect critical information effectively.
- Data at rest: Securing data while it is stored in databases, file systems, or other repositories is crucial. Encryption and access controls play a vital role in protecting data at rest.
- Data in transit: Encrypting data during transmission over networks (such as SSL/TLS) ensure that it remains confidential and protected from interception or tampering.
- Key management system: Establishing a robust key management system ensures the secure generation, storage, rotation, and destruction of encryption keys used to protect sensitive data.
- Certificates management: Managing and renewing digital certificates used for encryption and secure communication is essential to maintain trust and security.
5. Incident Response:
Establishing an incident response plan, managing logs, defining rules and alerts, and automating incident response processes play a significant role in minimizing the impact of security incidents.
Key aspects include:
- Incident response: Establishing an incident response plan to handle security incidents efficiently and minimize the impact on the organization.
- Log management: Collecting and analysing logs from various systems and applications to identify and respond to security incidents.
- Rules management: Defining rules and alerts to proactively monitor and detect security events or anomalies.
- Automated response: Automating incident response processes to accelerate response time and minimize manual errors.
To wrap up…
In an increasingly connected world, organizations must prioritize security requirements and adopt robust measures to protect sensitive data and meet regulatory obligations. By following this comprehensive guide, you have gained valuable insights into essential security requirements including identity management, detective controls, infrastructure security, data protection, and incident response. By implementing these measures, you can fortify your defences against potential cyberattacks, protect sensitive data, and ensure compliance with regulations. Remember, cybersecurity is a continuous effort that requires ongoing vigilance and adaptation to emerging threats. Stay informed about the latest security trends with Sensiple and regularly reassess your security practices. Your commitment to implementing these security measures is a crucial step towards a resilient and protected digital future.
About the Author
 Silambarasan Krishnan has over 18 years of expertise in Enterprise Cloud Services platform at Sensiple. He is presently the Principal Architect for "AWS and GCP Enterprise cloud services" Practice.
Silambarasan Krishnan has over 18 years of expertise in Enterprise Cloud Services platform at Sensiple. He is presently the Principal Architect for "AWS and GCP Enterprise cloud services" Practice.